Technological Axes
Technological Axes
Technological Axes

project offers.
Our strength lies in the collective. We create a bridge between public and private research in order to facilitate the transfer of technologies and skills. Join our research projects and let's develop together the technologies of tomorrow.

platforms offers.
Our technology platforms offer a full range of differentiating and multidisciplinary equipment in our four areas of expertise: materials & processes, energy, systems engineering and modeling, artificial intelligence and communications.
Three years after the launch of the initial SiCRET project, SiCRET+, a project which began in October 2023, is extending the scope of its study to include silicon carbide (SiC) power modules. The aim is to understand the ageing of power modules in normal and degraded operation, and in harsh environments (temperature, humidity, radiation), in order to derive predictive ageing models.
FREEzING 2
FREEzING 2, encouraged by the promising results obtained from FREEzING (2019-2023), starts at the beginning of March 2024. The aim of the project is to continue the development of durable icephobic surfaces using various surface treatment processes for aeronautical applications, and to assess their performances in a representative environment close to flight test.

The white paper “Ceramic matrix composites: a field of excellence in France” is now available. It is the fruit of the labours of Laurent Ferres, Director of the Bordeaux site, and our Aquitaine members and partners.
Portrait
Zeineb, an engineer and artificial intelligence project manager seconded by Thales, looks back on her career and experience at the IRT Saint Exupéry. Between project management and professional development, she recounts the highlights of her two years at the IRT. Interview.

DEEL (DEpendable and Explainable Learning) is a project, primarily a collaborative Franco-Quebec research team based in Toulouse (France) and Montreal (Quebec). Launched in 2018, its main objective is to develop new solutions for reliable and explainable machine learning.
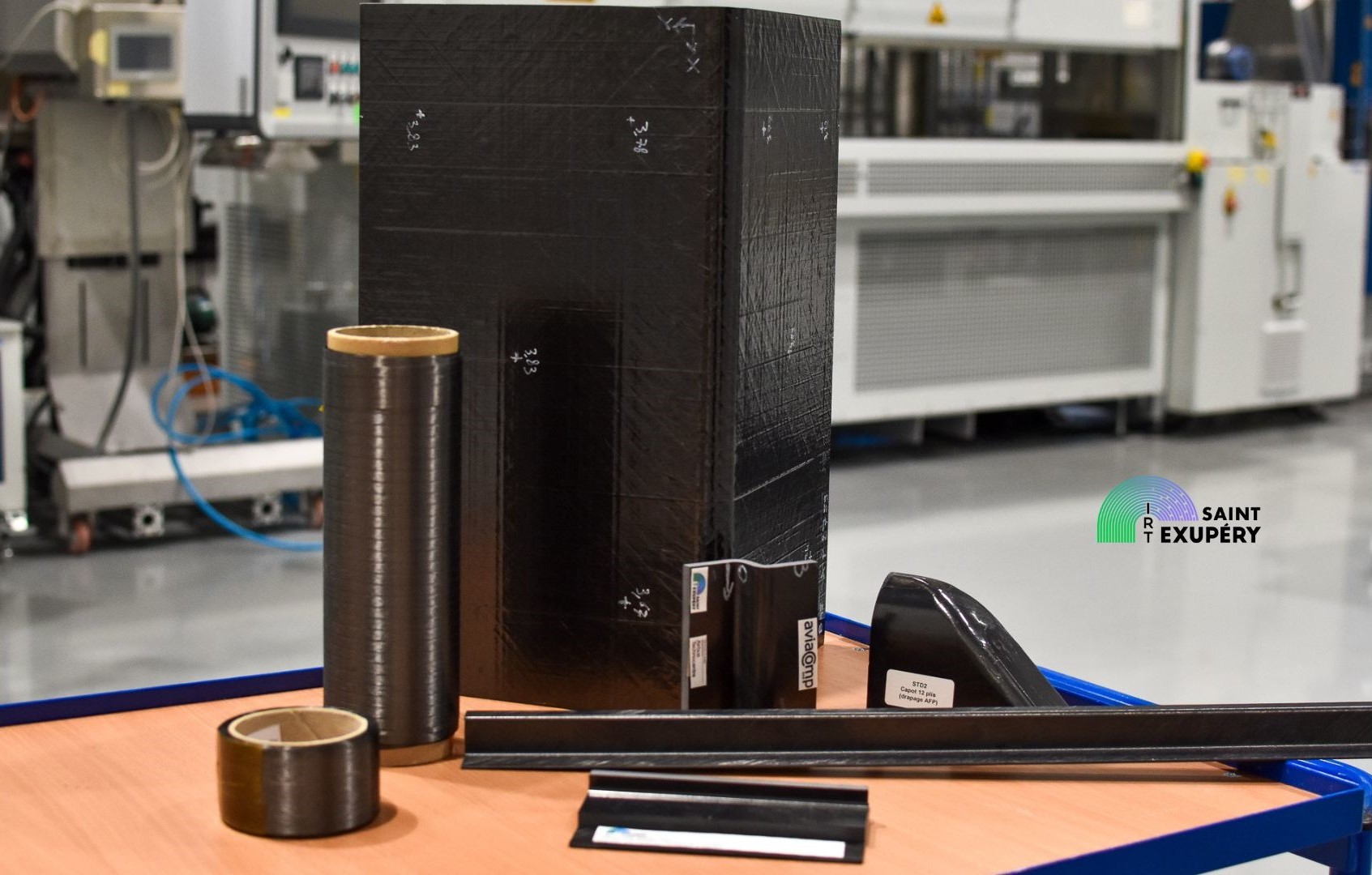
COMPINNOV TP2
2023 marks the end of the COMPINNOV TP2 project. Three years of research and development into high-performance thermoplastic composite semi-finished products, giving us a better understanding of the links between prepregs materials and manufacturing processes.
10 years

On Friday November 10, the IRT Saint Exupéry celebrated its 10th anniversary at the Cite de l'Espace in Toulouse, with employees from all three sites, members and partners. It was an opportunity to strengthen our ties and to start writing our plans for the coming years together.
Equality
The Gender Equality Plan (GEP) is a document produced by companies promoting actions in favor of gender equality...

Project

On April 21st, 2022, IRT Saint Exupéry held a press conference on the MAMA project (Metallic Advanced Materials for Aeronautics). During this occasion, IRT Saint Exupéry and the members of the project had the occasion to share and discuss about...